What are IT services?
IT services are services provided by companies or individuals to help organizations manage and maintain their information technology infrastructure. These services can range from hardware and software installation and maintenance to data backup and recovery, network and cybersecurity services, and more.
Phishing: The Art of Cybercrime

Key Takeaways:
Phishing is a type of cybercrime that aims to deceive individuals into revealing sensitive information.
Common types of include email phishing, smishing, and vishing.
To protect yourself, be wary of unsolicited messages, verify the source of messages, and avoid clicking on suspicious links.
LinkedIn takes action to tackle fake accounts

LinkedIn is introducing new verification features over the coming months to help tackle fake accounts.
Common Questions About Network Security

What is meant by network security?
Network security refers to the process of protecting computer networks from unauthorized access, hacking, theft, and damage to hardware, software, or electronic data. It involves implementing various measures, such as firewalls, antivirus software, encryption, access controls, and intrusion detection and prevention systems, to safeguard the network and the information it contains.
Here’s how to fix the most common VoIP issues

A piece of technology that claims to cut your expenses in half may seem too good to be true, and often, it is. But this isn’t the case with Voice over Internet Protocol (VoIP). Its promise of significantly reducing phone expenses is real and well-documented.
Two-Factor Authentication: What It Is and Why You Need It
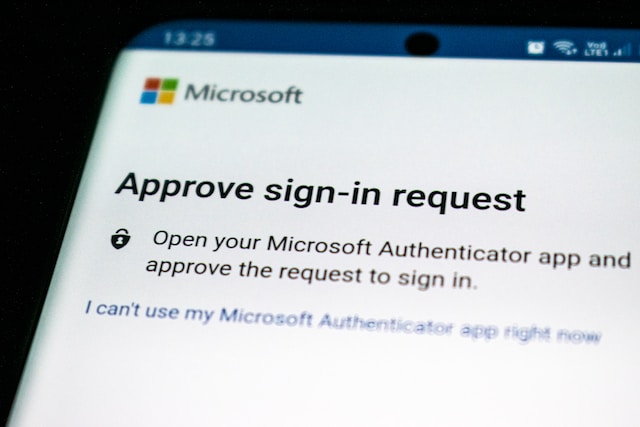
Two-factor authentication (2FA) is a security process that adds an extra layer of protection to your online accounts and systems.
2FA requires two forms of identification: something you know (like a password) and something you have (like a mobile phone or security key).
2FA can significantly reduce the risk of unauthorized access and protect your sensitive information from cyber threats.
The top FAQs about Ransomware

What is ransomware in simple terms?
Ransomware is a type of malicious software that hackers use to block access to a computer system or data until a ransom is paid. It works by encrypting the files on the victim's computer and demanding payment in exchange for the decryption key.
When to use Groups, Teams, and Yammer

In the digital age, businesses and organizations have a variety of collaboration tools at their disposal. With so many options available, it can be challenging to determine which tool is best suited for specific tasks and goals. Three commonly used tools in the Microsoft ecosystem are Groups, Teams, and Yammer.
What Does an IT Consultant Do?

Businesses are increasingly reliant on technology to improve their operations and stay competitive. As a result, the role of an IT consultant has become more critical than ever. An IT consultant is a professional who provides expert advice on how to use information technology to achieve business objectives.


